Computers & Technology
epub, pdf |eng | 1992-03-31 | Author:Neil Postman [Postman, Neil]
7 The Ideology of Machines: Computer Technology That American Technopoly has now embraced the computer in the same hurried and mindless way it embraced medical technology is undeniable, was perhaps ...
( Category:
Engineering
July 10,2017 )
epub |eng | 2017-02-23 | Author:C. J. Cherryh
8 Cabinet meeting. God. Shawn’s nine advisors, that met with him regularly, and that generally had compatible opinions—but no scarcity of concerns. There had been perhaps a few too many ...
( Category:
Computers & Technology
July 9,2017 )
epub |eng | 2017-02-27 | Author:Mark O'Connell
Long before the peoples of the Western World turned to the machine, mechanism as an element in social life had come into existence. Before inventors created engines to take the ...
( Category:
Internet & Social Media
July 9,2017 )
epub, pdf |eng | 2016-03-21 | Author:Andrew K. Dennis [Dennis, Andrew K.]
Following this, we then included the fb.h library, which gives us methods to access the frame buffer. You can read more about the library at https://www.kernel.org/doc/Documentation/fb/framebuffer.txt. After this we then ...
( Category:
Computers & Technology
July 9,2017 )
epub, azw3, pdf |eng | 2017-06-27 | Author:Evelina B. [B., Evelina]
inset Optional. Changes the shadow from an outer shadow (outset) to an inner shadow initial Sets this property to its default value. Read about initial inherit Inherits this property from ...
( Category:
Computers & Technology
July 7,2017 )
epub |eng | 2017-06-23 | Author:Andrei Besedin [Besedin, Andrei]
ArrayList represents dynamic Collection. Methods for manipulating elements are: add() – for adding element to ArrayList remove() – for removing elements from ArrayList get() – for getting elements from ArrayList ...
( Category:
Programming
July 7,2017 )
epub |eng | 2017-06-23 | Author:Miles Price [Price, Miles]
( Category:
Security & Encryption
July 7,2017 )
azw3, epub, pdf |eng | 2017-06-23 | Author:Miles Price
Physical security is a critical part of cyber security. Hackers will always look for any weakness that they can find, whether online or offline. Chapter 5: Social Engineering Did you ...
( Category:
Security & Encryption
July 7,2017 )
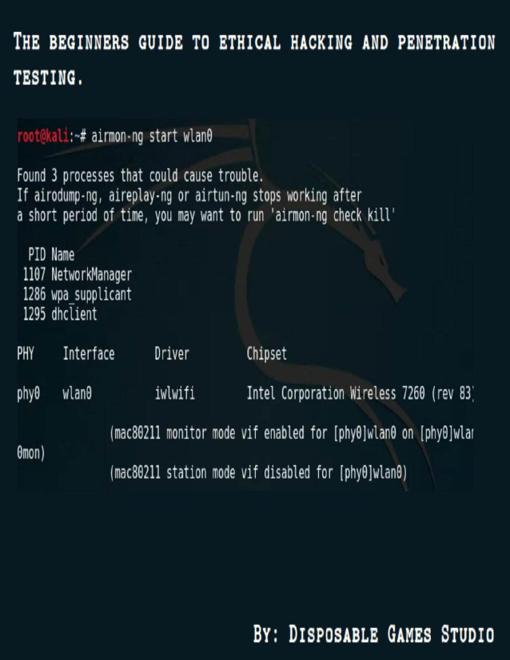
epub, azw3, pdf |eng | 2017-07-02 | Author:James Wells [Wells, James]
It shows you what was the permanent (built-in in network card) MAC address and its corporation in brackets, and down it shows that there is a new MAC address which ...
( Category:
Computers & Technology
July 5,2017 )
azw3, epub, pdf |eng | 2017-06-30 | Author:Jeff M
In the example above we clicked on the WirelessKeyView. This tool will scan the wireless network that the computer is currently connected to and display the network name, key type, ...
( Category:
Computers & Technology
July 4,2017 )
epub, pdf |eng | 2017-06-29 | Author:Serhan Yamacli [Yamacli, Serhan]
String weightStr = weightText.getText().toString(); double weight = Double. parseDouble(heightStr); Code 6.4 We now have weight and height data in double type variables so we can do the BMI calculation using ...
( Category:
Computers & Technology
July 3,2017 )
epub |eng | | Author:Manohar Swamynathan
# create hihger order polynomial for independent variables order_no = 6 # map the variable 1 & 2 to its higher order polynomial def map_features(variable_1, variable_2, order=order_no): assert order >= ...
( Category:
Programming
July 3,2017 )
epub |eng | 2014-09-15 | Author:James Robertson
( Category:
Performing Arts
July 1,2017 )
epub |eng | 2017-03-13 | Author:K.C. Wells [Wells, K.C.]
Chapter Fourteen JAMIE RINSED his mouth under the jet and then regarded himself in the mirror above the sink. What the fuck did I just do? He cupped his hands ...
( Category:
LGBT
July 1,2017 )
epub, mobi |eng | 2016-02-08 | Author:A M Eydie [Eydie, A M]
The more signatures that are from people you know and trust, the more trust you can have in the keys authenticity This trust stuff is a big deal for software ...
( Category:
Internet & Social Media
July 1,2017 )
Categories
Popular ebooks
Deep Learning with Python by François Chollet(24340)The Mikado Method by Ola Ellnestam Daniel Brolund(21601)
Hello! Python by Anthony Briggs(20835)
Secrets of the JavaScript Ninja by John Resig Bear Bibeault(19293)
Dependency Injection in .NET by Mark Seemann(18895)
The Well-Grounded Java Developer by Benjamin J. Evans Martijn Verburg(18510)
Kotlin in Action by Dmitry Jemerov(18288)
OCA Java SE 8 Programmer I Certification Guide by Mala Gupta(18119)
Algorithms of the Intelligent Web by Haralambos Marmanis;Dmitry Babenko(16978)
Adobe Camera Raw For Digital Photographers Only by Rob Sheppard(16947)
Grails in Action by Glen Smith Peter Ledbrook(16104)
Sass and Compass in Action by Wynn Netherland Nathan Weizenbaum Chris Eppstein Brandon Mathis(13799)
Secrets of the JavaScript Ninja by John Resig & Bear Bibeault(11805)
Test-Driven iOS Development with Swift 4 by Dominik Hauser(10636)
A Developer's Guide to Building Resilient Cloud Applications with Azure by Hamida Rebai Trabelsi(10590)
Jquery UI in Action : Master the concepts Of Jquery UI: A Step By Step Approach by ANMOL GOYAL(9732)
Hit Refresh by Satya Nadella(9099)
The Kubernetes Operator Framework Book by Michael Dame(8534)
Exploring Deepfakes by Bryan Lyon and Matt Tora(8358)
Robo-Advisor with Python by Aki Ranin(8302)